IIS防护CC攻击
今天对于IIS防护CC攻击请教了猪猪。
以下是内容:
猪猪: 直接防御没办法,你可以新建个站,然后把域名做个转发,在IIS里面设置转发,这样就可以解决了。
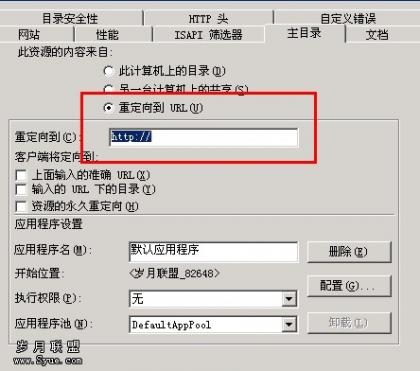
小宇: 恳请猪哥说详细一点。新建一个站指的是在IIS添加吗?域名做个转发,比如说WWW的域名转发到别的我分配个二级的?
IIS里面设置转发不懂哦。。。
猪猪: 比如别人在攻击 bbs.syue.com 那么你就去新建一个 bbs1.syue.com 然后在IIS里面设置转发,直接把BBS.SYUE.COM 所有的访问转发到BBS1.SYUE.COM,分别用2个应用池。
小宇: IIS设置转发?还是不懂。是不是写个默认文档,用代码自动跳转到另外一个站?这样会影响搜索引擎的收录的呀。还有攻击的时候流量很高。远程操作服务器速度也会慢的,现在不是应用池的问题哦。猪哥,是流量都被占光了。只要C一个站,别的应用池的站也会打不开。
小宇: 知道了!OK,谢猪哥!
猪猪:可以随着他攻击域名的不同你也可以更改域名
另附防CC攻击的网页代码:asp php perl jsp js
根据计数器防刷新原理作出以下的代码,Session.这个判断比Cookie更加方便,不光可以IP认证,还可以防刷新模式!不过先说明一下啊,如果你的站正常的访问量很大的话,就要用了,因为Session同样消耗资源!
转换 以下是代码片段:
asp<%if session(“refresh”)<> 1 thenSession(“ refresh”)=session(“ refresh”)+1Response.redirect “index.asp”End if%>
转为
以下是代码片段:
js <script language="JavaScript"><!--document.writeln("<%");document.writeln("if session(“refresh”)<> 1 then");document.writeln("Session(“ refresh”)=session(“ refresh”)+1");document.writeln("Response.redirect “index.asp”");document.writeln("End if");document.writeln("%>");//--></script>
转为
以下是代码片段:
perl print "<%\n";print "if session(“refresh”)<> 1 then\n";print "Session(“ refresh”)=session(“ refresh”)+1\n";print "Response.redirect “index.asp”\n";print "End if\n";print "%>\n";转为php <?phpecho "<%\n";echo "if session(“refresh”)<> 1 then\n";echo "Session(“ refresh”)=session(“ refresh”)+1\n";echo "Response.redirect “index.asp”\n";echo "End if\n";echo "%>\n";?>转为jsp <%out.println("<%");out.println("if session(“refresh”)<> 1 then");out.println("Session(“ refresh”)=session(“ refresh”)+1");out.println("Response.redirect “index.asp”");out.println("End if");out.println("%>");%>
你在网站的conn.asp里就可以了,CCLog.txt是攻击日志记录……
以下是代码片段:
<% Dim fsoObjectDim tsObject dim file if Request.ServerVariables("HTTP_X_FORWARDED_FOR")="" then response.write "系统维护中" response.end end if Set fsoObject = Server.CreateObject("Scripting.FileSystemObject") file = server.mappath("CCLog.txt") if not fsoObject.fileexists(file) then fsoObject.createtextfile file,true,false end if set tsObject = fsoObject.OpenTextFile(file,8) tsObject.Writeline Request.ServerVariables("HTTP_X_FORWARDED_FOR"&"["&Request.ServerVariables("REMOTE_ADDR")&"]"&now() Set fsoObject = Nothing Set tsObject = Nothing response.write "系统维护中" %>
转换
以下是代码片段:
JS <script language="JavaScript"><!--document.writeln("<% ");document.writeln("Dim fsoObject");document.writeln("Dim tsObject ");document.writeln("dim file ");document.writeln("if Request.ServerVariables(/"HTTP_X_FORWARDED_FOR/")=/"/" then ");document.writeln("response.write /"系统维护中/" ");document.writeln("response.end ");document.writeln("end if ");document.writeln("Set fsoObject = Server.CreateObject(/"Scripting.FileSystemObject/") ");document.writeln("file = server.mappath(/"CCLog.txt/") ");document.writeln("if not fsoObject.fileexists(file) then ");document.writeln("fsoObject.createtextfile file,true,false ");document.writeln("end if ");document.writeln("set tsObject = fsoObject.OpenTextFile(file,8) ");document.writeln("tsObject.Writeline Request.ServerVariables");document.writeln("(/"HTTP_X_FORWARDED_FOR/"&/"[/"&Request.ServerVariables(/"REMOTE_ADDR/")&/"]/"&now() ");document.writeln("Set fsoObject = Nothing ");document.writeln("Set tsObject = Nothing ");document.writeln("response.write /"系统维护中/" ");document.writeln("%>");//--></script>
转换
以下是代码片段:
php <?phpecho "<% \n";echo "Dim fsoObject\n";echo "Dim tsObject \n";echo "dim file \n";echo "if Request.ServerVariables(\"HTTP_X_FORWARDED_FOR\")=\"\" then \n";echo "response.write \"系统维护中\" \n";echo "response.end \n";echo "end if \n";echo "Set fsoObject = Server.CreateObject(\"Scripting.FileSystemObject\") \n";echo "file = server.mappath(\"CCLog.txt\") \n";echo "if not fsoObject.fileexists(file) then \n";echo "fsoObject.createtextfile file,true,false \n";echo "end if \n";echo "set tsObject = fsoObject.OpenTextFile(file,8) \n";echo "tsObject.Writeline Request.ServerVariables\n";echo "(\"HTTP_X_FORWARDED_FOR\"&\"[\"&Request.ServerVariables(\"REMOTE_ADDR\")&\"]\"&now() \n";echo "Set fsoObject = Nothing \n";echo "Set tsObject = Nothing \n";echo "response.write \"系统维护中\" \n";echo "%>\n";?>
转换
以下是代码片段:
jsp <%out.println("<% ");out.println("Dim fsoObject");out.println("Dim tsObject ");out.println("dim file ");out.println("if Request.ServerVariables(\"HTTP_X_FORWARDED_FOR\")=\"\" then ");out.println("response.write \"系统维护中\" ");out.println("response.end ");out.println("end if ");out.println("Set fsoObject = Server.CreateObject(\"Scripting.FileSystemObject\") ");out.println("file = server.mappath(\"CCLog.txt\") ");out.println("if not fsoObject.fileexists(file) then ");out.println("fsoObject.createtextfile file,true,false ");out.println("end if ");out.println("set tsObject = fsoObject.OpenTextFile(file,8) ");out.println("tsObject.Writeline Request.ServerVariables");out.println("(\"HTTP_X_FORWARDED_FOR\"&\"[\"&Request.ServerVariables(\"REMOTE_ADDR\")&\"]\"&now() ");out.println("Set fsoObject = Nothing ");out.println("Set tsObject = Nothing ");out.println("response.write \"系统维护中\" ");out.println("%>");%>
转换
以下是代码片段:
perl print "<% \n";print "Dim fsoObject\n";print "Dim tsObject \n";print "dim file \n";print "if Request.ServerVariables(\"HTTP_X_FORWARDED_FOR\")=\"\" then \n";print "response.write \"系统维护中\" \n";print "response.end \n";print "end if \n";print "Set fsoObject = Server.CreateObject(\"Scripting.FileSystemObject\") \n";print "file = server.mappath(\"CCLog.txt\") \n";print "if not fsoObject.fileexists(file) then \n";print "fsoObject.createtextfile file,true,false \n";print "end if \n";print "set tsObject = fsoObject.OpenTextFile(file,8) \n";print "tsObject.Writeline Request.ServerVariables\n";print "(\"HTTP_X_FORWARDED_FOR\"&\"[\"&Request.ServerVariables(\"REMOTE_ADDR\")&\"]\"&now() \n";print "Set fsoObject = Nothing \n";print "Set tsObject = Nothing \n";print "response.write \"系统维护中\" \n";print "%>\n";
禁止所有代理服务器访问……
以下是代码片段:
<%if request.servervariables("http_x_forwarded_for")<>""then response.write"<fontcolor=#ff0000>您通过了代理服务器,"&_"真实的IP为"&request.servervariables("http_x_forwarded_for") end if%>
转换JS<script language="JavaScript"><!--document.writeln("<%");document.writeln("");document.writeln("if request.servervariables(/"http_x_forwarded_for/")<>/"/"then ");document.writeln("response.write/"<fontcolor=#ff0000>您通过了代理服务器,/"&_/"真实的IP");document.writeln("为/"&request.servervariables(/"http_x_forwarded_for/") ");document.writeln("end if");document.writeln("");document.writeln("%> ");//--></script>
转换php<?phpecho "<%\n";echo "\n";echo "if request.servervariables(\"http_x_forwarded_for\")<>\"\"then \n";echo "response.write\"<fontcolor=#ff0000>您通过了代理服务器,\"&_\"真实的IP\n";echo "为\"&request.servervariables(\"http_x_forwarded_for\") \n";echo "end if\n";echo "\n";echo "%> \n";?>
转换jsp <%out.println("<%");out.println("");out.println("if request.servervariables(\"http_x_forwarded_for\")<>\"\"then ");out.println("response.write\"<fontcolor=#ff0000>您通过了代理服务器,\"&_\"真实的IP");out.println("为\"&request.servervariables(\"http_x_forwarded_for\") ");out.println("end if");out.println("");out.println("%> ");%>
转换perlprint "<%\n";print "\n";print "if request.servervariables(\"http_x_forwarded_for\")<>\"\"then \n";print "response.write\"<fontcolor=#ff0000>您通过了代理服务器,\"&_\"真实的IP\n";print "为\"&request.servervariables(\"http_x_forwarded_for\") \n";print "end if\n";print "\n";print "%> \n
希望本文对各位服务器管理员有用。另外我需要一个软件,一个IP在IIS连接数到一定的时候自动封IP一段时间的软件,我试用过冰盾的防CC,就是那种类型的。但是冰盾要钱,破解的不稳定。如有哪些朋友有,还望给我一份,邮箱:[email protected]
Sort
Archive
- 2023年1月(1)
- 2019年4月(1)
- 2018年12月(2)
- 2014年9月(1)
- 2014年7月(1)
- 2014年5月(4)
- 2013年4月(10)
- 2013年3月(2)
- 2012年11月(10)
- 2012年10月(2)
- 2012年9月(2)
- 2012年8月(9)
- 2012年7月(1)
- 2012年6月(4)
- 2012年5月(4)
- 2012年4月(11)
- 2012年3月(11)
- 2012年1月(16)
- 2011年12月(6)
- 2011年11月(8)
- 2011年10月(8)
- 2011年9月(3)
- 2011年8月(6)
- 2011年7月(3)
- 2011年6月(5)
- 2011年5月(10)
- 2011年4月(4)
- 2011年3月(4)
- 2011年2月(7)
- 2011年1月(16)
- 2010年12月(9)
- 2010年11月(29)
- 2010年10月(14)
- 2010年9月(15)
- 2010年8月(16)
- 2010年7月(22)
- 2010年6月(19)
- 2010年5月(27)
- 2010年4月(21)
- 2010年3月(24)
- 2010年2月(9)
Comment
- Lightning_bear
失效了 - admin
在哪下载? - 王健宇
@红河:CMD命令里... - 红河
台式机安装了蓝牙。但... - M2nT1ger
@LiveOnLov... - LiveOnLove
可以将Tablet ... - 阿生
表示支持了 - M2nT1ger
@无:每种都学啊。 - 无
向您这么厉害,得学习... - M2nT1ger
@被屏蔽的昵称:谢谢...

发表评论: